Crypttech
Authentication Management
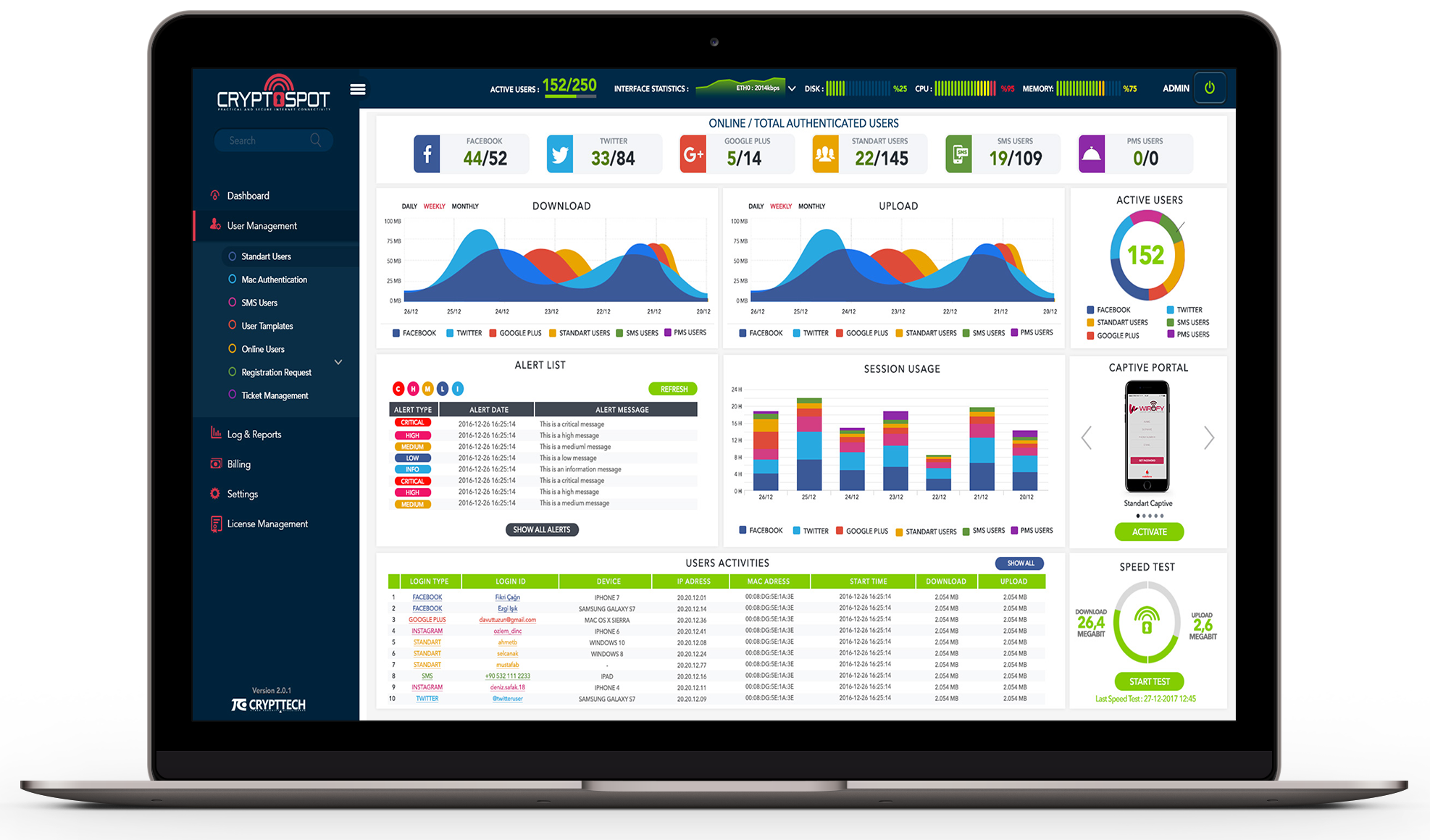
Crypttech CryptoSpot - Practical and Secure Internet Connectivity
CRYPTOSPOT is a gateway software that helps you share your wired or wireless internet access and provide it to your customers and / or visitors. By using CRYPTOSPOT, you can authorize a traveler, your customers or your employees for safe, fast and easy internet access.
CRYPTOSPOT not only provides you a reliable internet access with charge or free of charge to your network but also provides statistical reporting information and data storage. When connected to the network, the user is authorized with the welcome page. It can be integrated by SMS, AD (Active Directory), National Identity Sources, Web Service, Social Media, Rest API, Sponsor Mail, Hotel-Visitor Programs and Front Office Software.
Key Features and Advantages
- Secure internet gateway for customers, visitors and a specific network
- Hardware and vendor independent, easy to install HotSpot server
- Variety in authorization methods
- Usage templates, access profiles and user configuration flexibility
- Location based welcome page, IP-MAC, white-black lists, URL filtering
- Bandwidth / Quota management, defining access limits
- Access without authentication, redirect after login
- SMS, Social Media, Sponsor, PMS (Front Office), Standard Users, Web Services authentication
- Statistical dashboards, web access records, executive reports
- Customized welcome pages, mobile / tablet compatibility, multi-language support
- Advertising / Digital Marketing and survey management
- RESTful API support for integration and development
Cyber Orchestration Automation and Response
Crypttech SOAIR - Next Generation Solutions in Security Operations
SOAIR manages the process of responding and deciding for the incidents occurring at corporations by providing a dynamic and flexible infrastructure. It works integrated with almost all security products. It provides a flexible integration and API layer for non-integrated systems. It offers a unique case & response management system with an advanced workflow and an artificial intelligence system on its own.
Key Features and Advantages
- Easy to Create & Built-in Visual Playbooks
- Automated Workflows
- Predefined İntegrations & Connectors
- Embedded Next Gen CRYPTOSIM Platform (SIEM) Integration
- Microservice Architecture
- Automated Incident Management & Response
- Threat Monitoring & Investigation & Hunting
- Alert Triage and Prioritization
- Customizable Dashboards
- Advanced Reporting
- Unlimited Scalability
- Improved Efficiency of Security Teams
- Multitenancy for MSSPs
- AI Based Workflow & Playbook Creation
- On-Prem & On-Cloud Deployment
Cognitive Security Information and Event Management
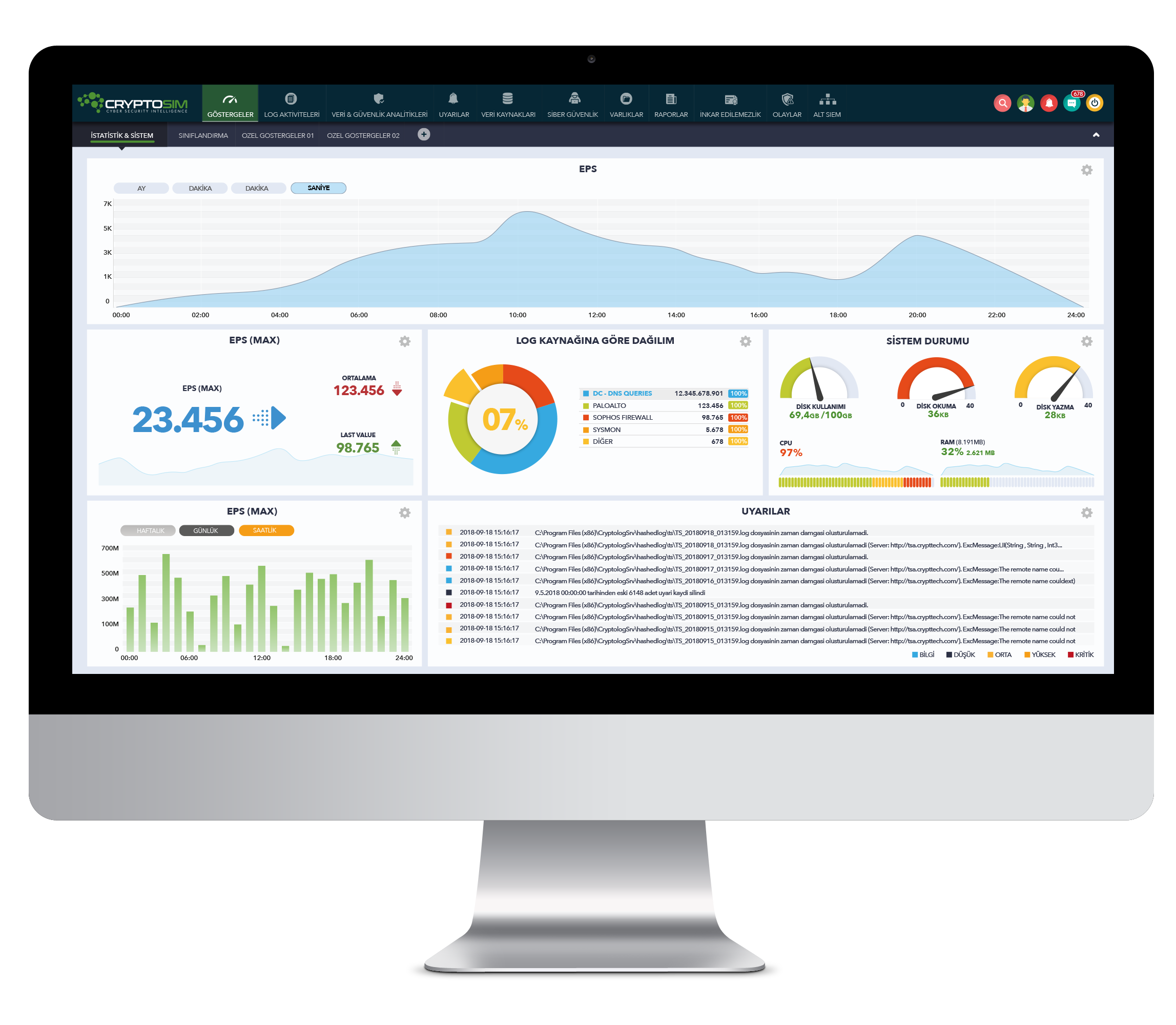
Crypttech CSIEM - Cognitive Security Information and Event Management
SIEM stands for Security Information and Event Management. It is a software solution that collects and analyzes security data from various sources, such as network devices, servers, and applications. SIEM is an essential component of any modern cybersecurity strategy, and is used by organizations of all sizes and industries.
CSIEM provides contextual and situational awareness developed on a purely cognitive architecture and designs a self-learning & developing SIEM. This product was developed entirely with Artificial Intelligence architectures and algorithms.
CSIEM uses rules-based or machine learning-based algorithms to perform event correlation, and can be customized to meet the specific needs of an organization.
CSIEM AI-based anomaly detection is a powerful tool for SIEM solutions, which can help organizations to detect and respond to security threats more quickly, accurately, and efficiently.
CSIEM solutions can incorporate threat intelligence feeds from various sources, such as CRYPTTECH CTI, commercial threat intelligence providers, open-source feeds, and internal sources.CSIEM can also use threat intelligence to perform predictive analysis, by identifying potential security threats before they occur and taking proactive measures to prevent them.
CSIEM can generate various types of compliance reports, such as audit reports, incident response reports, and compliance scorecards, which provide a detailed view of an organization’s security posture and compliance status. CSIEM can also automate compliance reporting, which reduces the time and effort required to prepare and submit compliance reports, and ensures that the reports are accurate and up-to-date.
CSIEM solutions can provide forensic data, such as network traffic logs, system logs, and application logs, which can be used to reconstruct the sequence of events leading up to a security incident.
- Real-time threat detection and analysis
- Event correlation
- Anomaly detection
- Threat intelligence with CTI
- Machine Learning and Deep Learning Methods for faster and more accurate threat detection
- Advanced graph data structures and AI algorithms runs on CRYPTTECH GRAPH
- Fully AI-based UEBA Features
- Centralized log management and retention
- Automated incident response and remediation via SOAIR
- Compliance reporting and auditing
- Forensic analysis
- Scalability and performance
- Integration with other security tools
- Easy of use
Data Loss Prevention & Data Classification Solution
Crypttech VATOS DLP - Solution for Enterprise Data Loss Prevention & Data Classification
Data Loss Prevention (DLP) system is a security software developed for the protection of sensitive data.
VATOS DLP comes with a variety of built-in policies, varying from compliance to appropriate usage to intellectual property, allowing you to match entire and partial documents to a robust set of guidelines, ensuring that all of your confidential information, both known and unknown, is protected.
VATOS DLP integrates with data transmission gateways utilizing simple mail transfer protocol (SMTP) or ICAP-compliant web proxies to help you implement policies for data leaving the network through email, webmail, instant messaging, wikis, blogs, portals, HTTP/HTTPS, and FTP transfers.
Key Features and Advantages
- Web-Based Central Management
- Big Data Infrastructure
- Content Control
- Device Control
- Auto Discovery Capability
- Application Control
- Network-Based Control
- Fingerprint Capability
- LDAP Integration (Windows and Linux)
- Control and Control at the Operating System Kernel Level
- Horizontal and Vertical Scalability with Microservice Architecture
- Container (Docker) Based Architecture
- Artificial Intelligence Based Automatic and Manual Classification
- OCR, ICR Capability
- Fast Policy and Event Log Transmission
- Customizable Agent Alerts
- Email Notifications
- Windows / Linux Support
Log Management
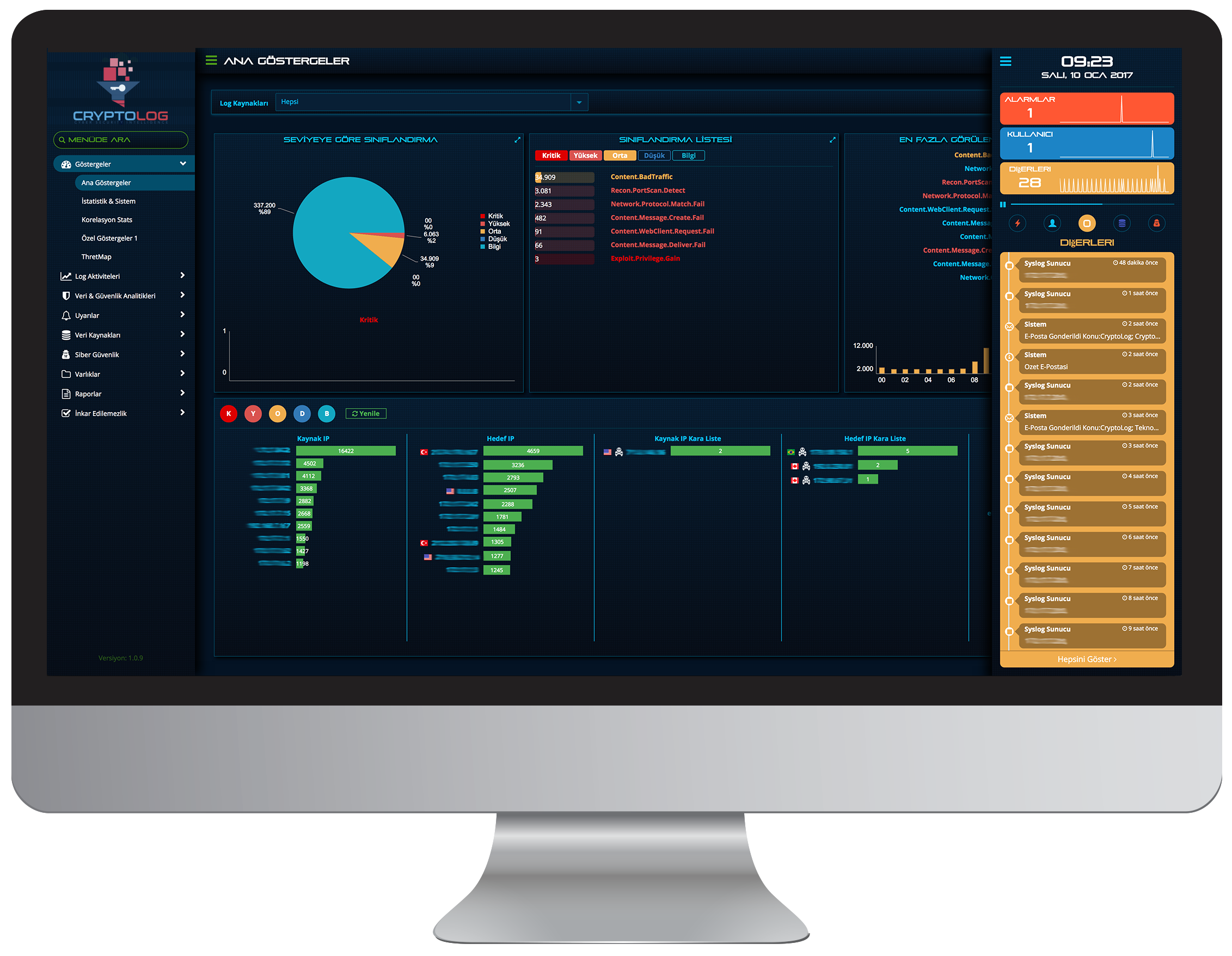
Crypttech CryptoLog - Innovative Approaches and Big Data Analysis in Log Management
CRYPTOLOG is a cost-effective integrated log management system that helps you meet regulatory compliance on the one hand, while reducing your security risks in a variety of IT environments. With its fast and powerful engines, CRYPTOLOG brings together a wide range of log and events to give you a comprehensive view of all your network activities on a customizable panel. It groups and categorizes events and generates useful information in detailed analysis for anomaly detection to help forensic investigations.
CRYPTOLOG combines all the logs and places timestamps in cases where the source of the attacks is safely monitored due to the engine functions of the nonrepudiation feature. CRYPTOLOG complies with log storing regulations, International Non Repudiation Standards, Stock Exchange Commission regulations, Banking Regulatory and Supervisory board, and standards such as ISO 27001.
Key Features and Advantages
- Comprehensive approach to many log types and collection methods
- Alert mechanism according to recording content and condition
- Detailed forensic analysis with advanced search engine
- Scalable infrastructure and architecture by business size
- High performance in log collection, processing and reporting
- Compliance with up-to-date legislation and standards
- Flexible archiving, backup and storage
- Easy applicability for complex topologies
- Ability to work on multiple platforms
- Detailed categorization by log type
- Full-text search over indexed data
Vulnerability Management
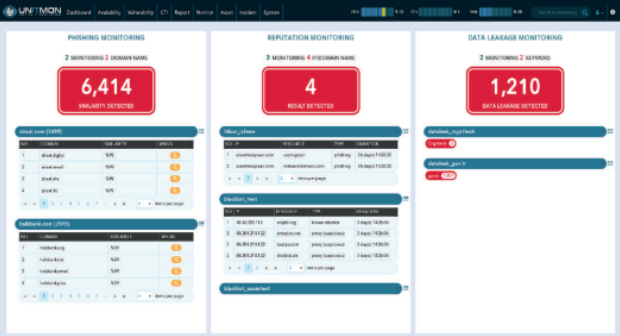
Crypttech Unitmon - Unified IT Monitoring, Catch all details
UNITMON is a web based monitoring tool that not only gives you the ability to instantly check your website, but also allows you to search your network capabilities and controls the performance of your network components via a user-friendly interface. It also reduces maintenance costs and critical failure risks at the key points of your IT infrastructure by providing intelligence about the security of your web content, your server and your application.
Key Features and Advantages
- Executive Dashboards
- HTTP / S, SOAP, Web Service Monitoring
- Web Application Monitoring
- Server Performance Monitoring
- Website / Server Security Vulnerability Monitoring
- SMS, EMail Notification
- Distributed, Scalable Architecture, Location Based Controls
- Cyber Intelligence Service Controls
- Phishing Domain Name Controls
- Autonomous Vulnerability Scanning Schedules
- Leaked Data Analysis
- Paste Site Controls
- Social Media Monitoring