Veriato
User Activity Monitoring (UAM) and User and Entity behavior Analytics (UEBA) in One Platform
Productivity Monitoring, Threat Detection, Investigation and Compliance
Modern businesses all around the world use Veriato’s adaptable user activity monitoring solutions for compliance, cyber security, and productivity.
Employee Productivity
Employee Productivity Monitoring For Your Workforce
Tools that are strong and simple to use to keep your office, hybrid, and remote teams productive.
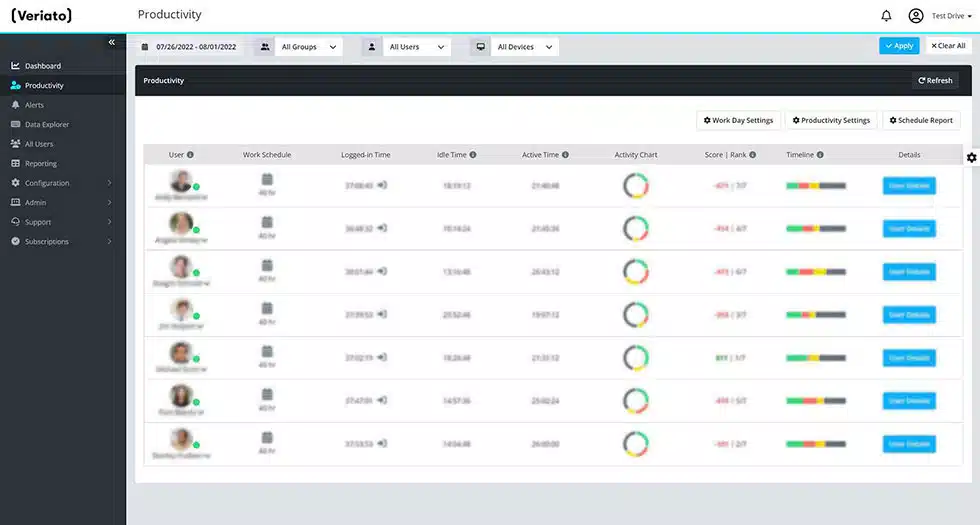
Idle and Active Time Tracking
The AI-powered system behind Veriato examines user behavior trends and instantly notifies you of any unusual or questionable conduct.
Web & Application Use
Assign productivity scores to websites, programs, and applications.
Screenshots
Select between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
File & Document Tracking
Keep track local activities, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Fully Customizable Settings
Decide on flexible work schedules for each team or department, as well as the times of day when tracking begins and stops.
Reports & Real-Time Alerts
Select from a variety of pre-made reports or customize your own. Create real-time alerts that fit your productivity indicators.
Workplace Investigations
Strong Workplace Investigation Tools
Veriato helps your company detect financial fraud, data theft and other employee misconduct.
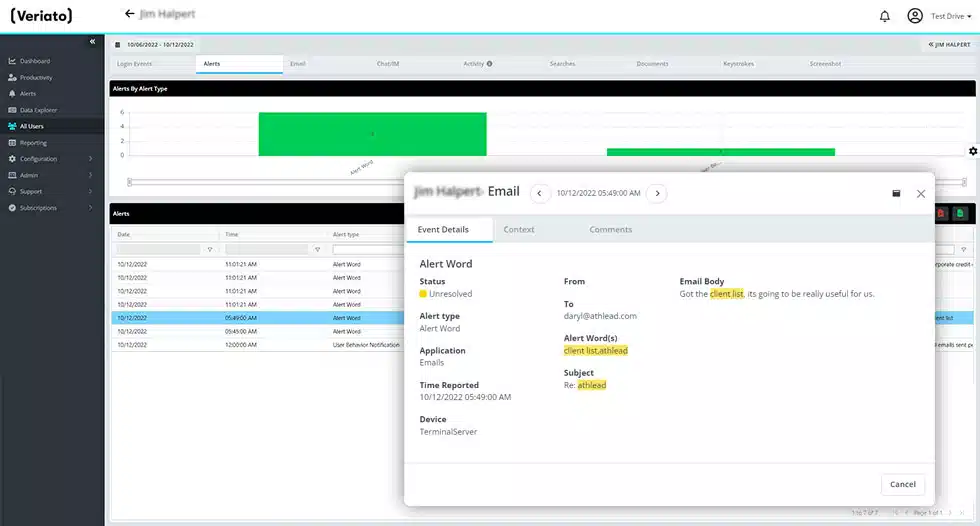
Web, Chat, and IM Activity
Observe and document communications activities on widely used messaging platforms. Keep track of every web activities, including file uploads and webmail access.
Email Monitoring
Record and examine communication activity using both conventional email applications and a variety of well-liked webmail providers.
Screenshots
Choose between the Continuous, Keyword Triggered, and Activity Triggered screenshot types.
Application Tracking
To offer accurate reports on what applications are being utilized, by whom, and for how long, track all application usage.
Keystroke Logging
Every keystroke, including those containing “secret” characters and sequences, is recorded, and real-time warnings are sparked in response to certain keywords.
Tracking Files & Documents
Follow print activity as well as actions taken with local, removable, and cloud storage. Check the creation, editing, deletion, and renaming of files.
Auditing & Compliance
Smarter Auditing & Compliance
Veriato optimizes your audit readiness while reducing the administrative cost of business or regulatory compliance.
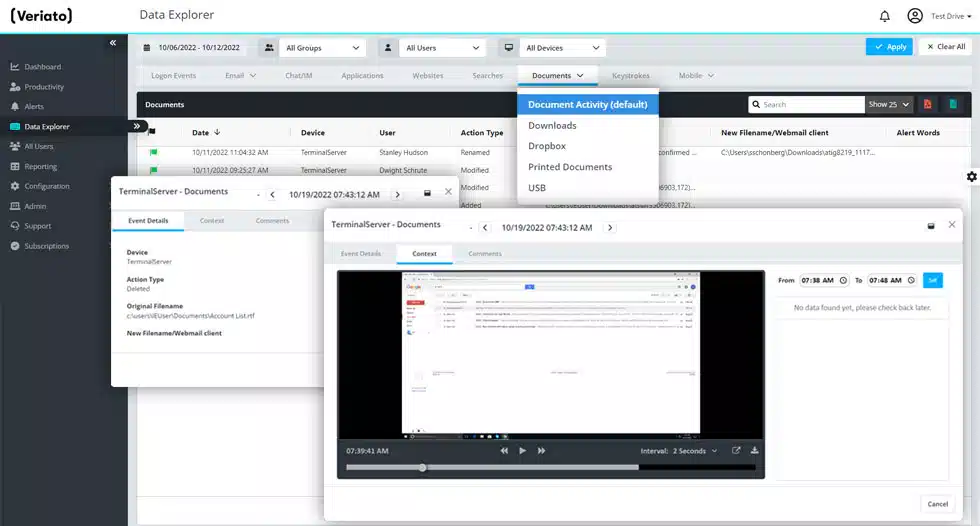
User Activity Monitoring
Monitor activity across applications, email, chats, files, the internal network, the online, and much more to ensure compliance.
Psycholinguistics Analysis
Determine the writer’s sentiment by identifying the opinions conveyed in email text.
Real-Time Alerts & Reports
Receive real-time notifications and reporting anytime possible fraud or unlawful conduct is found.
Screenshots
Choose between the Continuous, Keyword Triggered, and Activity Triggered screenshot types.
Network Activity
Automatically record connections made by programs, including the ports utilized and the bandwidth used.
Tracking Files & Documents
Follow print activity as well as actions taken with local, removable, and cloud storage. Check the creation, editing, deletion, and renaming of files.
Insider Risk Management
AI-Driven Insider Risk Detection
Veriato protects your organization from insider threats with predictive behavior analytics and user activity monitoring.
Application Tracking
Captures all application usage to provide true reporting on what applications are being used, by who, and for how long.
Psycholinguistic Analysis
Identify opinions expressed in email text to determine the writer’s sentiment.
Screenshots
Choose between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
Email Monitoring
Capture and analyze communication activity in traditional email clients as well as many popular webmail services.
Network Activity
Autonomously capture connections made by applications, including ports used and bandwidth consumed.
File & Document Tracking
Track activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Veriato Works Everywhere
Android Android 4 – 13
Windows Pc Windows 7 – 11
Mac MacOS 10.8 – 12
Chromebook *All Chromebooks
*Hp, Asus, Dell, Lenovo, Acer, Samsung & Google
