HOPEX Enterprise Risk Management
HOPEX Enterprise Risk Management
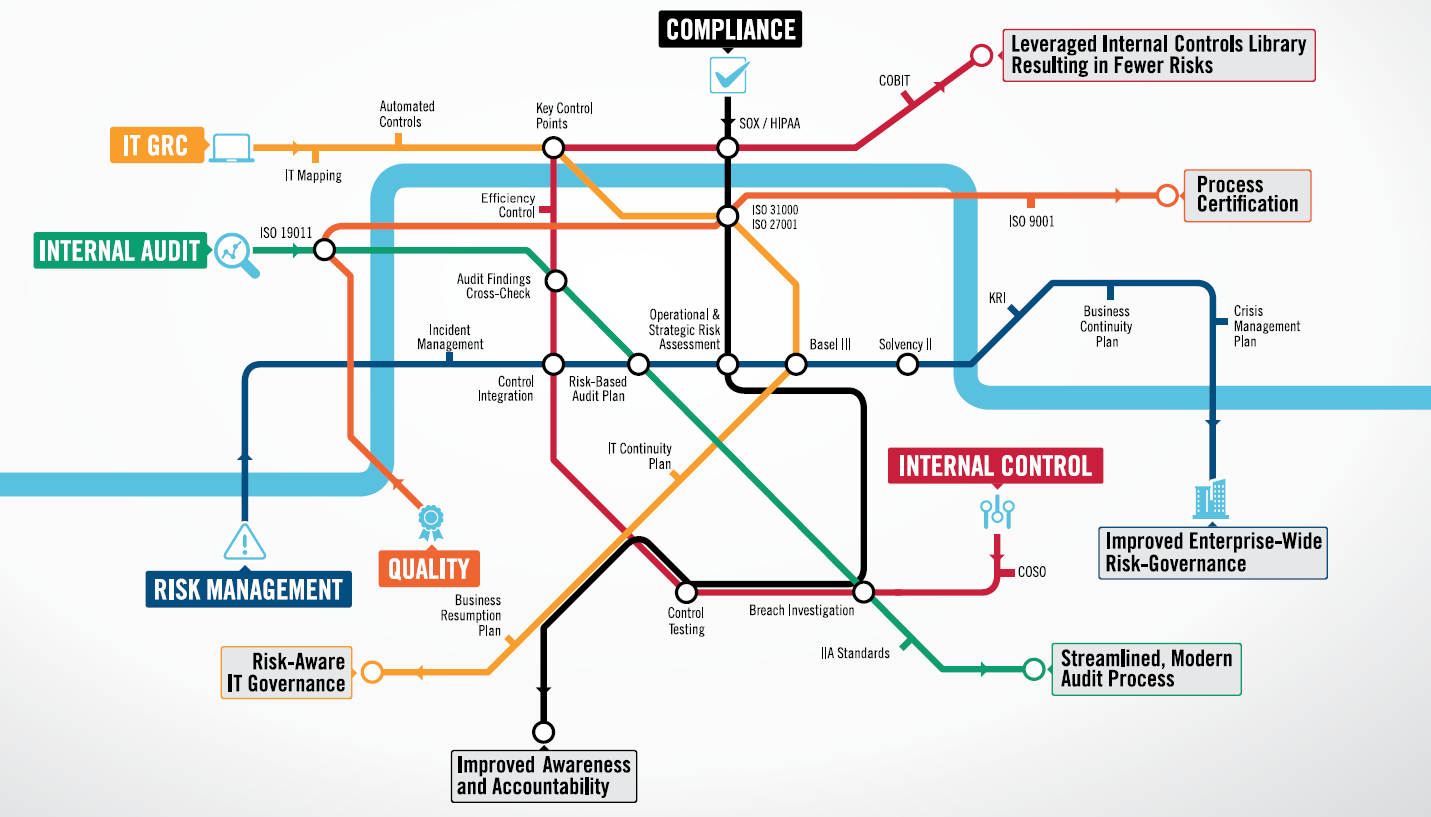
HOPEX Enterprise Risk Management (ERM), one of the modules of the HOPEX GRC product family, helps you manage the wide spectrum of risks and related operations in your organization, from identifying risks to generating reports. Moreover, while doing all these, it also guarantees data consistency and quality.

HOPEX Enterprise Risk Management (ERM) risk management units and in your institution;
Increases effectiveness and quality: It enables the establishment and management of a structured risk library in a common repository where all changes are tracked. This step is also important as it facilitates inspections. Automated risk assessment surveys also lighten the workload of risk managers, allowing them to focus on tasks that require less or no repetition.
It ensures that risks are evaluated together with business units and users: Each participant in the process has a specific interface where they can see only the information within their own responsibility. In addition, there is a collaborative workspace that allows multiple departments to work together comfortably. This structure enables the collection of input from business units and users to assist in the assessment of risks and controls. All exchanges between risk managers and business unit users can be tracked and automated.
Allows automation of communication and consolidation: Advanced
It enables you to standardize and automate the collection, analysis and reporting of IT risks and their business impact so that you can evaluate and control your organization’s Information Technology (IT) resources and infrastructure.
It meets the needs of traditional IT administrators, IT Risk managers, IT Security Managers and IT Compliance Managers:
- Identifying threats and vulnerabilities of applications, system technologies, and other IT resources
- Identification and assessment of applications and IT risks that may arise from their deployment
- Identification and evaluation of IT security controls of applications
- Reporting of IT control levels and regulatory compliance summaries
- Qualitative assessment of IT suppliers and consultants
Its comprehensive features in the categories of IT risk assessment, IT compliance risk assessment, and IT vendor risk assessment support you and your organization.
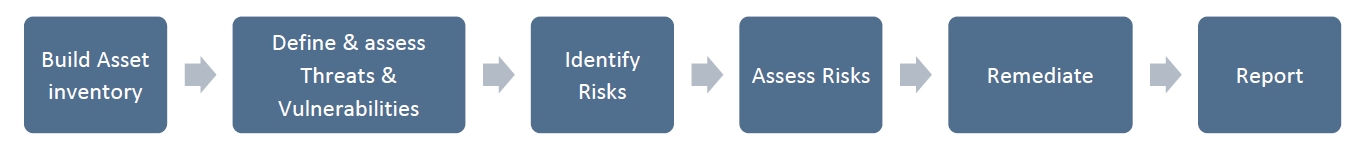
IT risk assessment provides deep impact analysis that includes changes and the impact of these changes on your IT infrastructure, data and capacity by creating a resource inventory, identifying threats and vulnerabilities, identifying and assessing risks, generating solutions and reporting the solution produced.
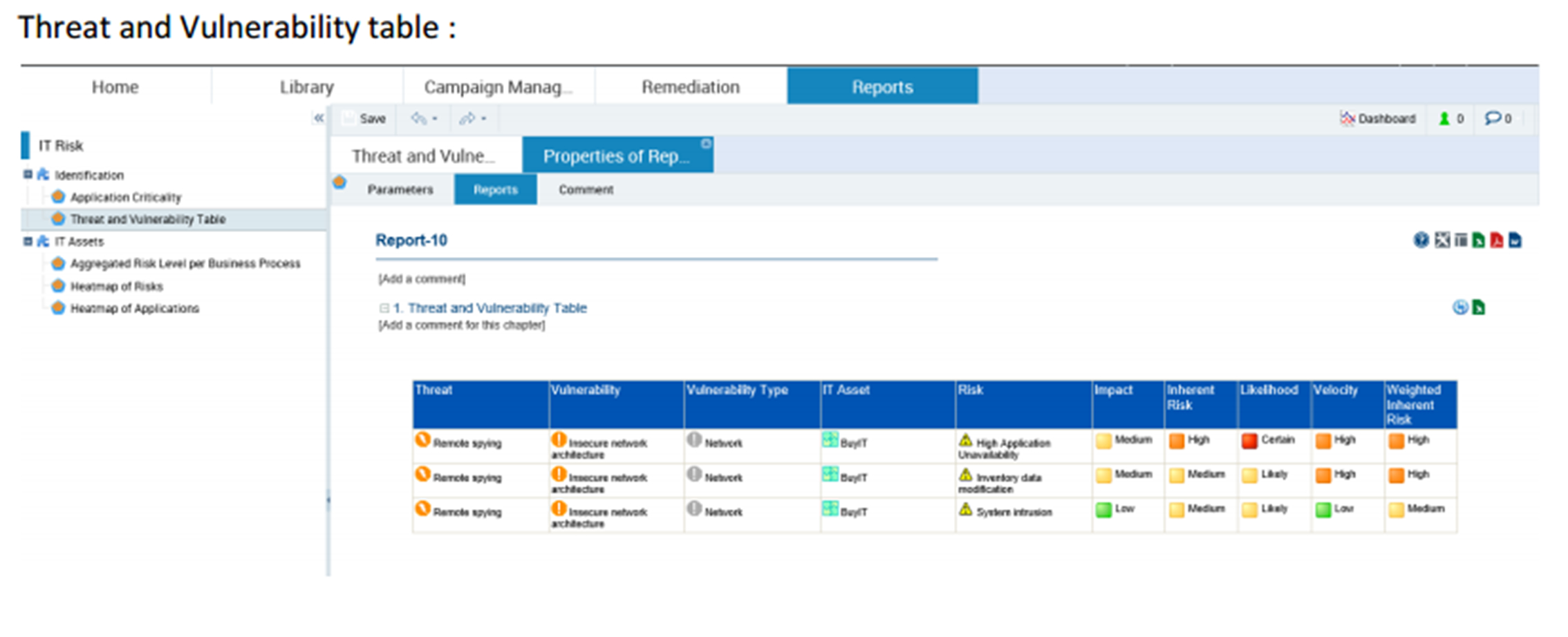
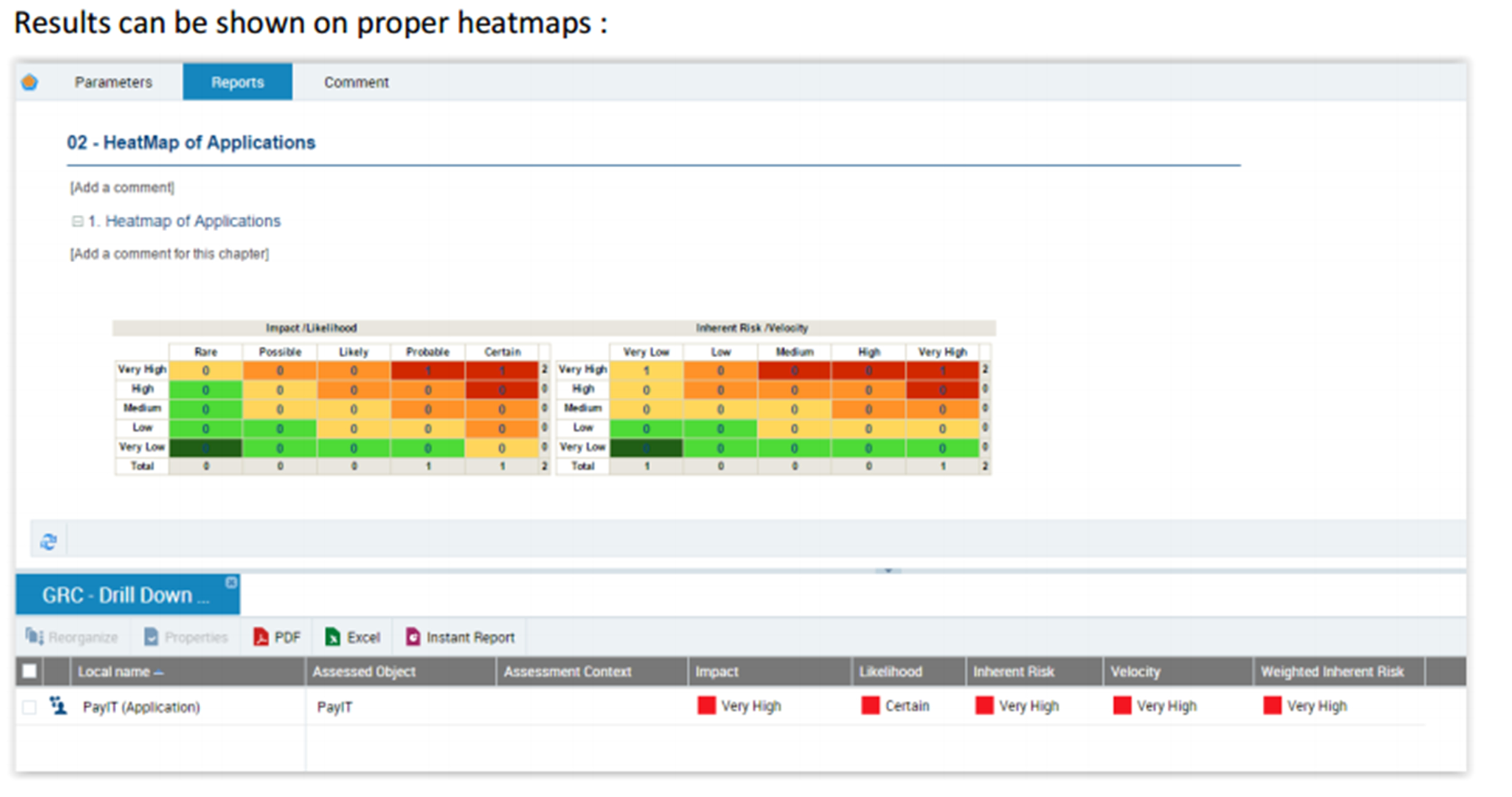
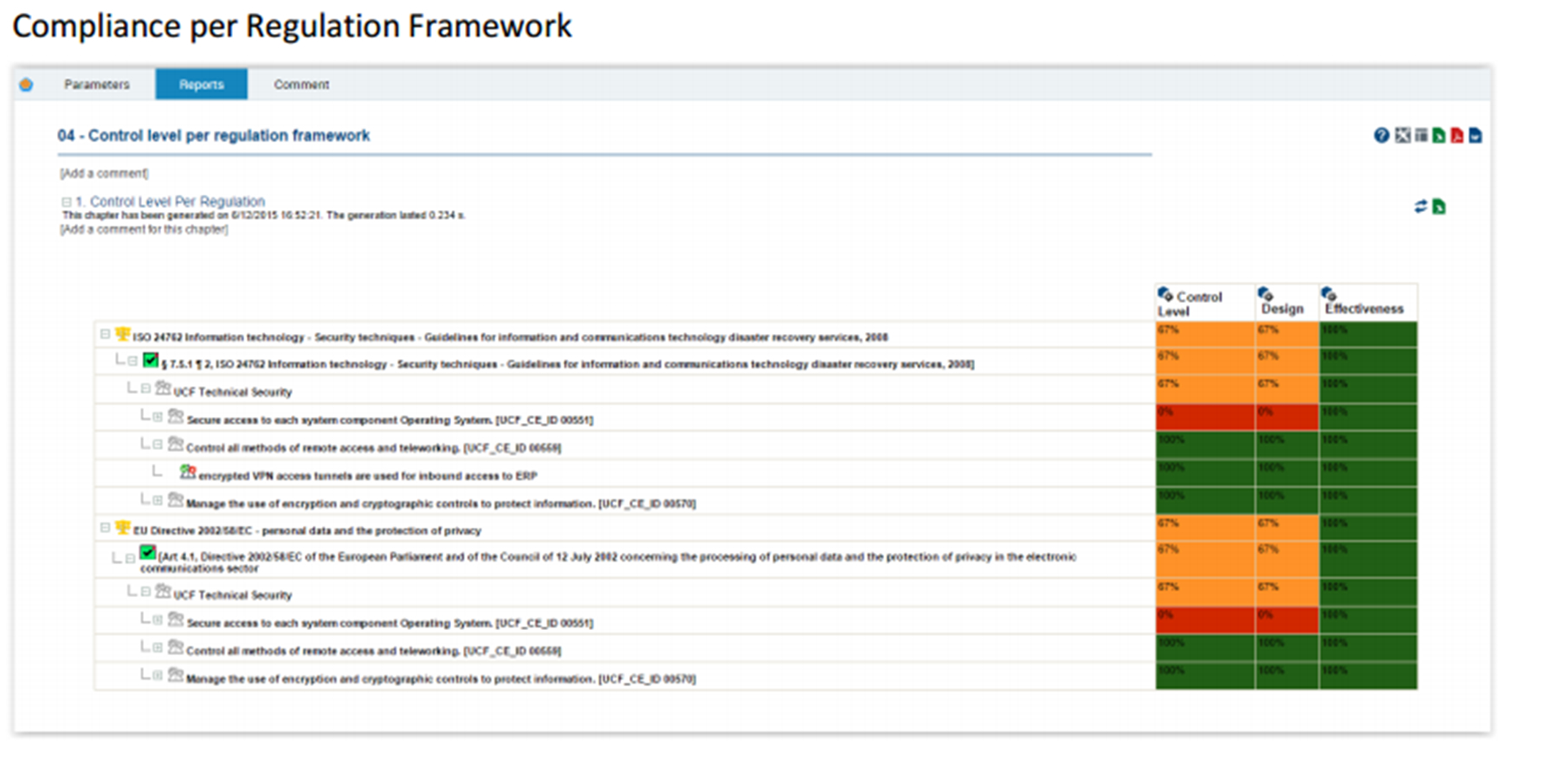
IT regulatory compliance risk assessment
The IT compliance process uses the regulatory repository. After all the legislation is imported, the controls are created and collected in a repository. These two steps enable the compliance assessment to be performed and the relevant reports to be obtained.

Checklist: By control type, status, legislative infrastructure
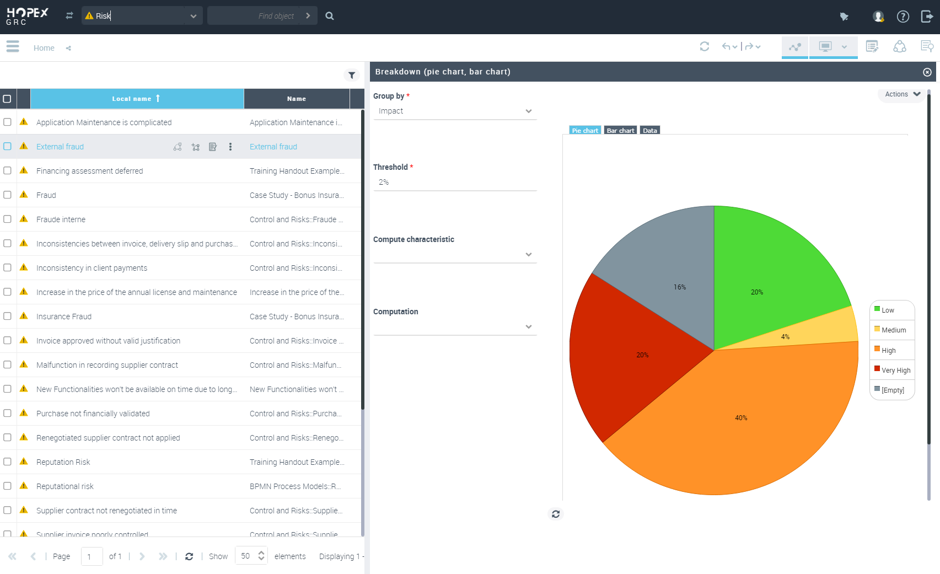
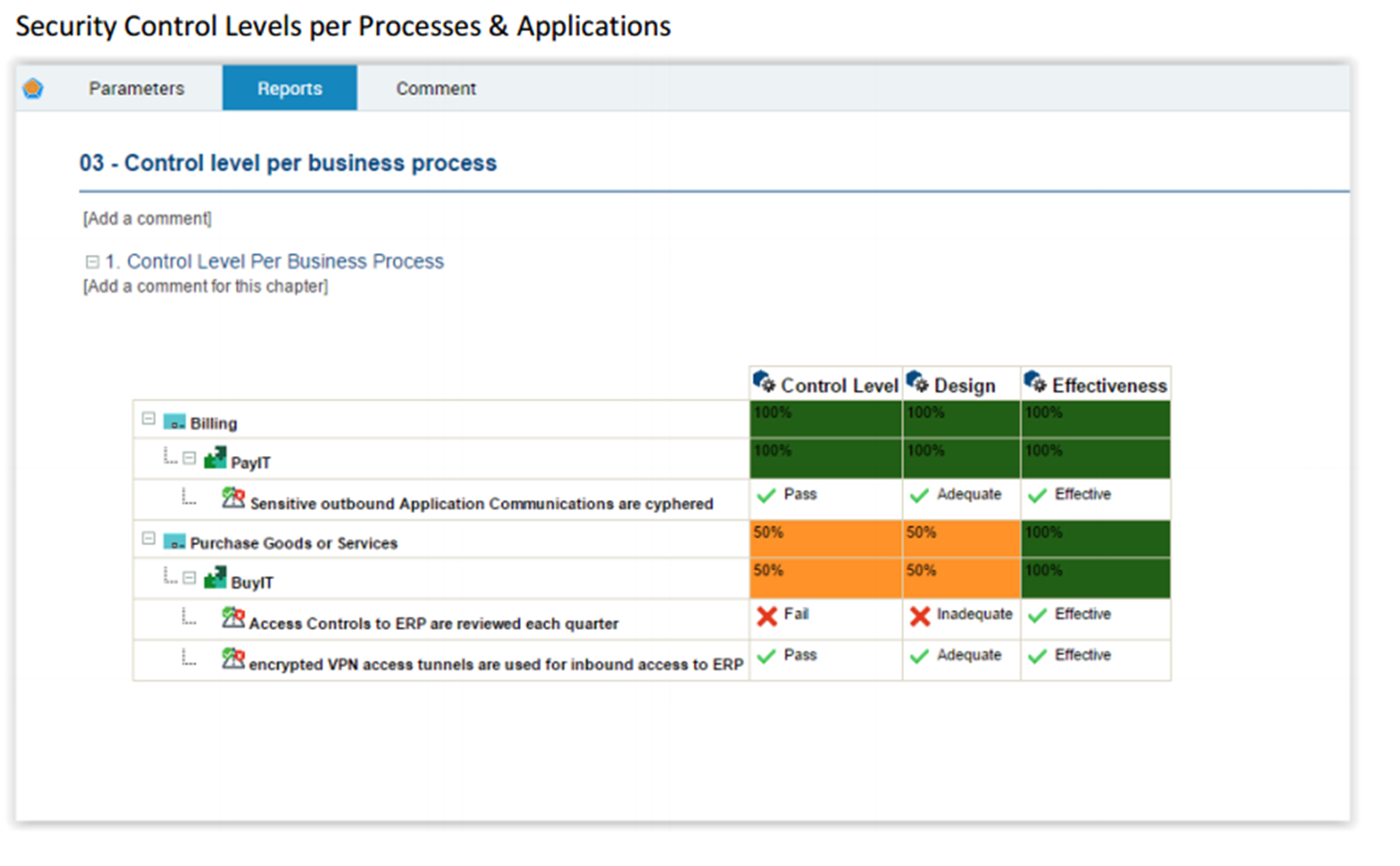
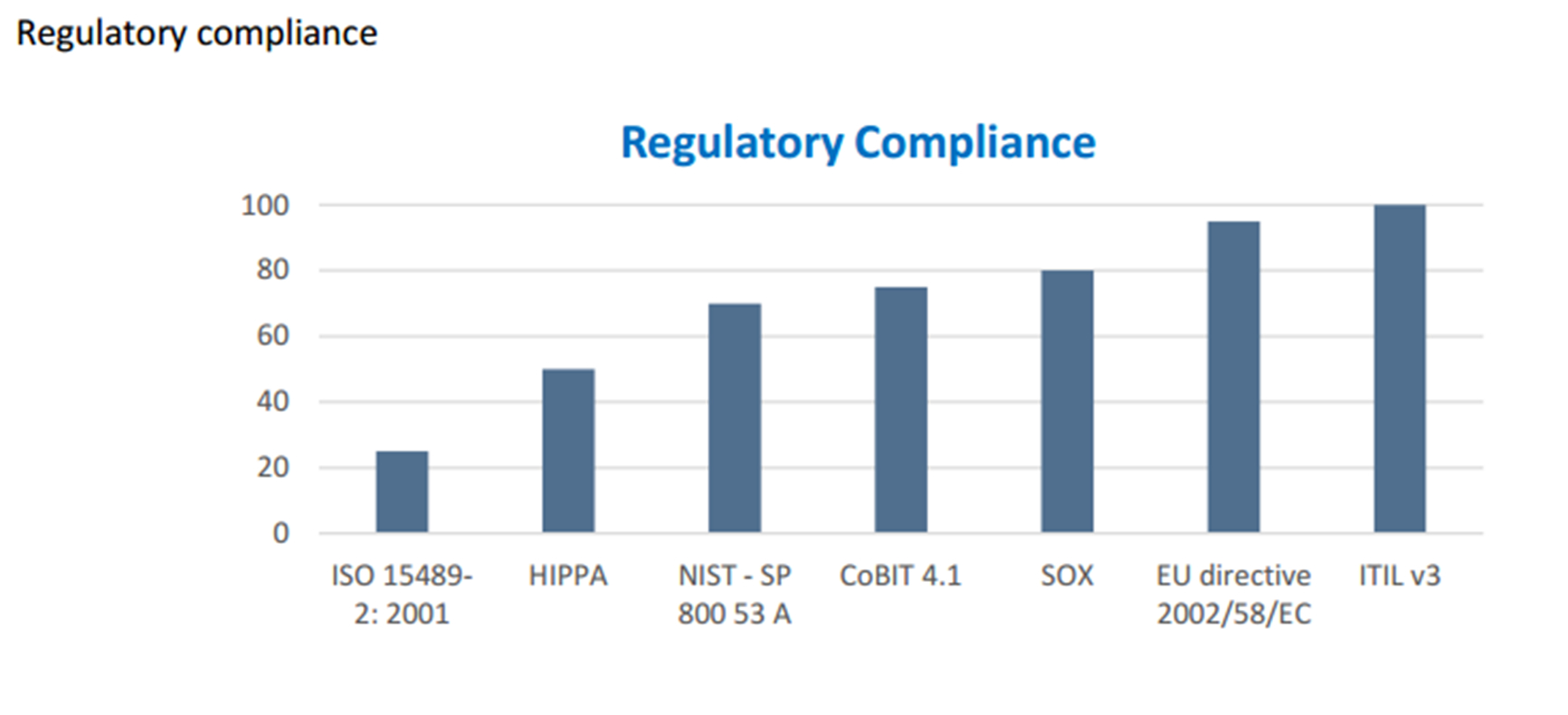
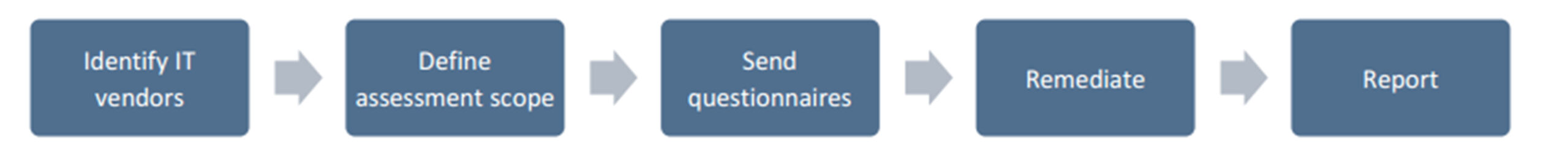
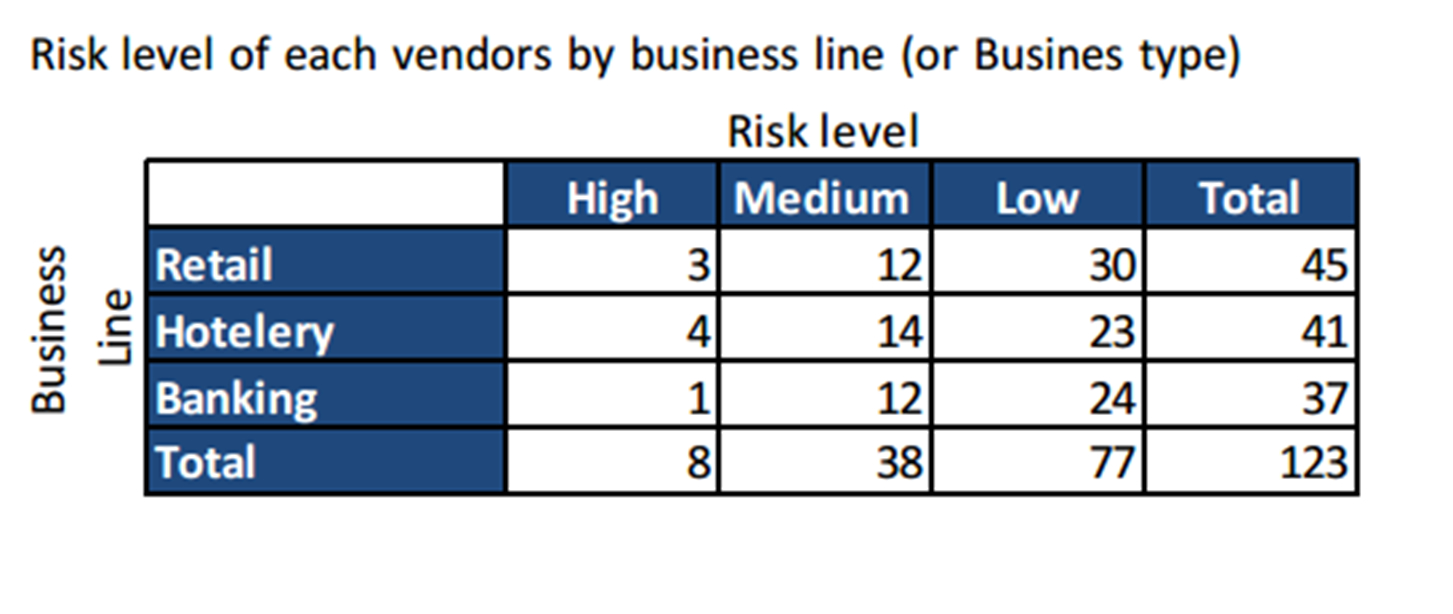
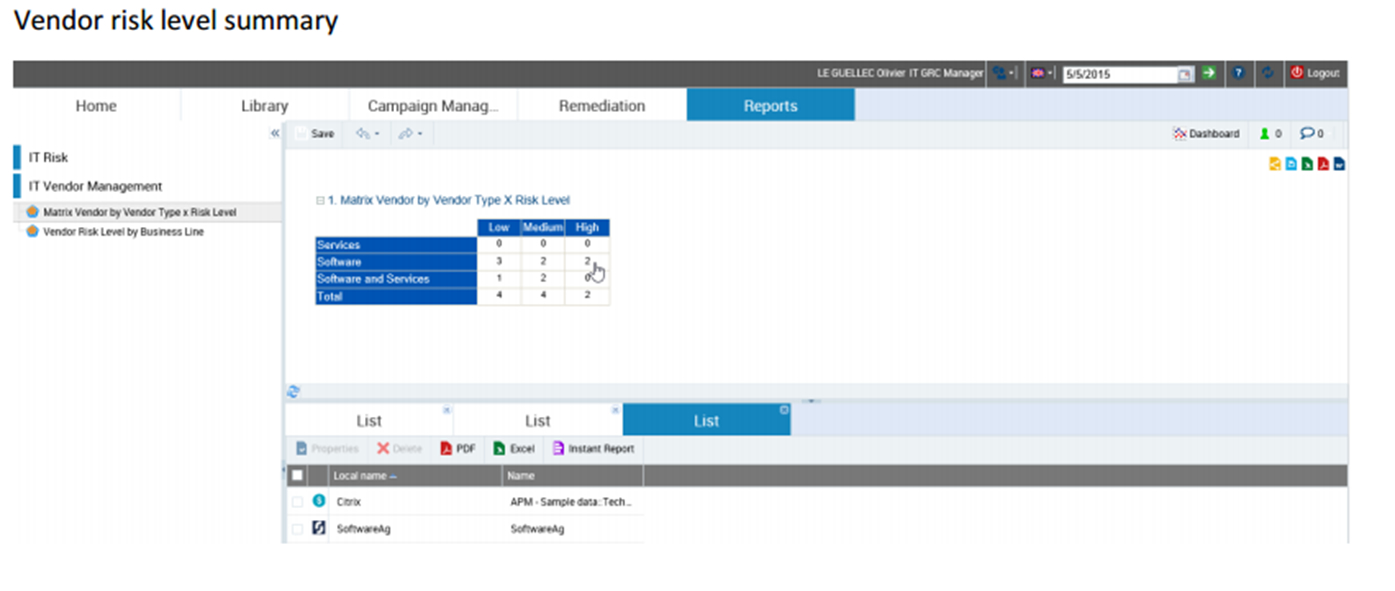
IT vendor risk assessment
The IT vendor evaluation methodology uses a proprietary database. This database is based on survey-based assessments submitted to eligible owners in the institution. After the suppliers are identified and the scope of the assessment is defined, the assessments are sent to the relevant owners. Results are analyzed so that action plans and reports can be triggered.
MEGA’s platform built on the central repository ensures that all your GRC goals reach each other.